

What happens when cybercriminals wield the stealth of spies and the greed of gangsters in a single devastating blow? A chilling wave of ransomware attacks sweeping across Latin America and the Asia-Pacific region offers a grim answer, highlighting the urgent need for stronger defenses. Storm-2603,

In an era where software vulnerabilities can lead to catastrophic breaches impacting millions of users and costing billions in damages, the urgency to embed security into every stage of development has never been more critical. The National Institute of Standards and Technology (NIST), a pivotal US

In an evolving threat landscape where cyberattacks continue to grow in sophistication, hypervisor-level ransomware emerges as a critical concern for businesses globally. These advanced threats involve attacks on the hypervisor layers of virtual machines, bypassing traditional security measures to

Rupert Marais, a recognized security specialist in endpoint and device security, sheds light on the intricate world of Chinese state-sponsored hacking and the cyber espionage ecosystem. With a focus on Silk Typhoon and its affiliated firms, his insights help us understand the operational frontiers

Navigating the New Digital Reality How far would individuals go to safeguard their online identity amid increasing scrutiny? In the wake of newly imposed age restrictions in the UK, an astonishing 1,400% surge in VPN sign-ups reflects a growing demand for digital privacy. This spike underscores the

In today’s increasingly connected world, having reliable access to Wi-Fi is indispensable. Picture arriving at a familiar location where your Windows laptop connects seamlessly to the Wi-Fi, yet your Android phone and other devices are left in the lurch with forgotten passwords. For many, this
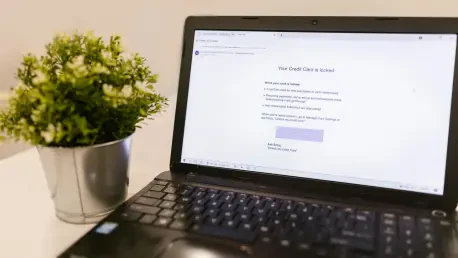
Today's digital landscape presents a paradox: while many organizations have embraced advanced cybersecurity measures for their systems, email security often lags behind, reminiscent of outdated antivirus solutions from decades past. As attackers increasingly target email systems with sophisticated

Cybersecurity is continuously challenged by evolving malware threats, and the resurfacing of Lumma Stealer is a testament to this ongoing struggle. After being disrupted by law enforcement, this notorious malware has quickly reemerged, employing more sophisticated and stealthier tactics that

The digital realm, often perceived as an enigmatic domain, became the backdrop for a significant courtroom episode involving a British student. In a severe blow to cybercrime, Ollie Holman, a young British student, received a seven-year prison sentence for orchestrating a vast cyber-fraud

The vision of Britain as a leading AI superpower is taking shape as colorful yet challenging, requiring innovative solutions in energy and investment strategies. A detailed exploration of this domain reveals significant growth within the EMEA bitbarn market, underlined by notable statistics and
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy