
I'm thrilled to sit down with Rupert Marais, our in-house security specialist with deep expertise in endpoint and device security, cybersecurity strategies, and network management. Today, we're diving into a critical issue in the realm of software supply chain security—a recently discovered flaw in

In an era where cyber threats evolve at an unprecedented pace, Palo Alto Networks, a globally recognized leader in cybersecurity, has introduced a transformative suite of solutions to confront the dual challenges of quantum computing risks and the intricacies of multi-cloud environments. This
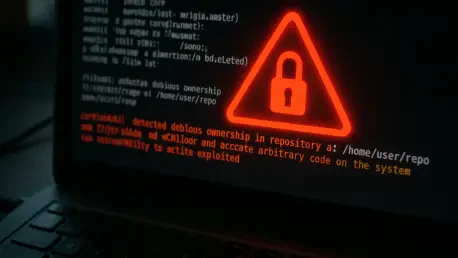
In a deeply alarming development for the tech community, a critical vulnerability in Git, identified as CVE-2025-48384, has emerged as a prime target for attackers, with active exploitation already underway, posing a severe risk to developers and organizations worldwide. This flaw, embedded in the

Imagine a scenario where a trusted colleague calls with an urgent request for sensitive data, only to later discover it was a hacker in disguise. This chilling reality struck Workday, a leading AI-driven platform for HR and payroll management used by over 11,000 organizations globally, including

Introduction Today, we’re thrilled to sit down with Rupert Marais, our in-house security specialist with extensive expertise in endpoint and device security, cybersecurity strategies, and network management. With cybercriminals constantly evolving their tactics, Rupert offers a deep dive into the

Imagine a digital army of tens of thousands of compromised devices, silently waiting to unleash chaos on unsuspecting targets across the globe. This is the reality of RapperBot, a formidable botnet that has emerged as a leading tool for distributed denial-of-service (DDoS) attacks. Operating as a