
In the intricate and rapidly shifting world of IT security, a subtle yet profoundly dangerous issue has emerged as a critical concern for organizations worldwide: the persistent access rights known as standing privilege. These always-on permissions, often granted to users or systems without a
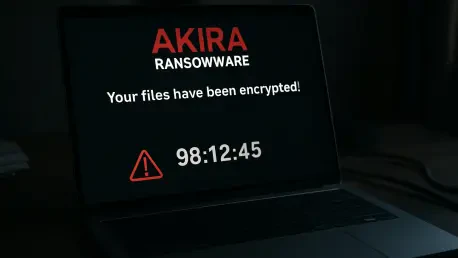
What happens when a trusted shield becomes the very gateway for chaos? In the realm of cybersecurity, SonicWall SSL VPN appliances, long relied upon for secure remote access, have turned into prime targets for a ruthless adversary: the Akira ransomware group. Since late July, these devices have

In the ever-evolving digital realm, WordPress stands as the backbone of countless websites, commanding an impressive 60.8% market share among content management systems (CMS), and its ubiquity makes it an irresistible target for cybercriminals. Powering everything from personal blogs to sprawling

In the ever-shifting landscape of cybersecurity, a hacking collective known as Scattered Spider has emerged as a significant challenge, targeting industries ranging from retail to transportation with alarming precision. Linked to The Com online criminal network, this group has demonstrated a knack

In a staggering breach of digital trust, a sophisticated phishing attack recently infiltrated the npm ecosystem, a cornerstone of JavaScript development, compromising packages that collectively amass over 2 billion weekly downloads. This incident not only exposed the fragility of open-source

What happens when the invisible keys to a digital kingdom fall into the wrong hands? Tokens, those small but mighty components of authentication, quietly power access to everything from personal apps to sprawling enterprise systems, and when mismanaged, they can unlock chaos, paving the way for