
A single compromised password can unravel an entire digital life in minutes, a reality that has become starkly apparent as cybercrime reports continue to climb, yet remarkably common and weak passwords like '123456' persist in widespread use. In this environment, relying on a password alone is akin
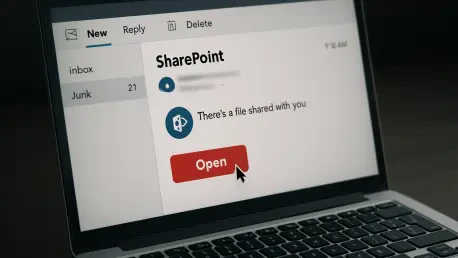
The very digital collaboration tools designed to foster productivity and seamless information sharing are increasingly being weaponized by sophisticated threat actors, turning trusted platforms into Trojan horses for widespread cyberattacks. A recent, highly-coordinated campaign has brought this

The traditional world of channel sales, long reliant on static training manuals and periodic webinars, is confronting a profound and necessary disruption. As technology solutions grow exponentially more complex and market demands for specialized expertise intensify, the established methods of

A newly discovered set of three critical zero-day vulnerabilities within the mcp-server-git , a reference implementation for the Model Context Protocol (MCP), has exposed a significant security gap in AI-driven development environments. These flaws, rooted in inadequate input validation and

The security of personal information held by government agencies became a pressing concern as two separate data breaches at state-level Departments of Human Services were announced within a two-week period, collectively exposing the sensitive data of nearly one million residents in Illinois and

The rapid integration of artificial intelligence into enterprise environments has created a landscape where powerful new tools are being deployed at an unprecedented pace, but this rush to innovate often overshadows a critical examination of the underlying security posture of the frameworks these