Today, we’re joined by Rupert Marais, our in-house security specialist, to dissect a critical vulnerability that has once again shaken the Node.js ecosystem. We’ll be exploring a severe sandbox escape flaw in the popular vm2 library, a tool designed to run untrusted code safely. Our discussion will cover the technical mechanics behind this exploit, the troubling pattern of recurring vulnerabilities in JavaScript sandboxing, and the broader defense-in-depth strategies developers must adopt to achieve true isolation.
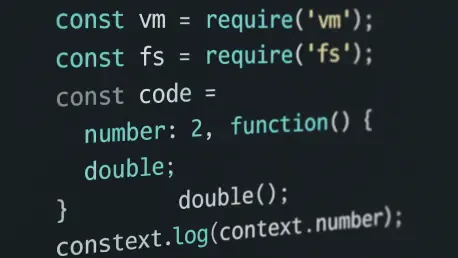
The critical vm2 vulnerability, CVE-2026-22709, involves improper Promise handler sanitization. Could you walk us through the technical details of how an attacker could leverage this flaw to escape the sandbox and what the practical impact of arbitrary code execution looks like in this scenario?
Absolutely. The heart of this vulnerability, which scores a frightening 9.8 on the CVSS scale, lies in a subtle but critical oversight in how vm2 handles Promises. The library is built to intercept and proxy JavaScript objects to keep sandboxed code from touching the host system. It was correctly sanitizing local Promise handlers, but the researchers at Endor Labs found that async functions actually return globalPromise objects. The library failed to properly sanitize the then and catch methods on these global Promises. This created a direct escape vector. For an attacker, it’s like finding an unguarded back door. Once they trigger this flaw, they break free from the sandbox’s constraints and can run code directly on the underlying server, giving them the ability to read sensitive files, connect to other systems on the network, or install malware.
Considering the history of recurring sandbox bypasses in vm2, what does this pattern reveal about the inherent challenges of securing JavaScript sandboxes? Please share your perspective on why the project was resurrected after being discontinued and what this implies for long-term user trust.
This steady stream of bypasses, including seven others just in the last couple of years, paints a very clear picture: creating a truly secure JavaScript sandbox is extraordinarily difficult. The proxy-based model used by vm2 attempts to wrap and control every interaction, but the language is so dynamic that new edge cases and escape methods are constantly being discovered. It’s a high-stakes cat-and-mouse game. The project’s brief discontinuation in July 2023, announced by the maintainer Patrik Simek, was a moment of stark honesty about the immense challenge. Its resurrection late last year, with active maintenance now confirmed for the 3.x versions, shows there’s still a huge demand for this kind of tool. However, for developers, this history should be a major red flag. It erodes trust and underscores that relying solely on a single library for security, especially one with such a track record, is a risky bet.
Developers are urged to update to vm2 version 3.10.3 for critical patches. Looking beyond this immediate fix, what is the core architectural difference between vm2’s proxy-based model and an alternative like isolated-vm that uses V8’s native Isolate interface? Please elaborate on these technical distinctions.
The architectural difference is fundamental. Vm2 operates by wrapping objects in proxies at the JavaScript layer, essentially trying to build a cage out of software rules. It intercepts calls to prevent the sandboxed code from accessing forbidden host resources. The problem, as we’ve seen, is that if you miss even one type of interaction, like the globalPromise handlers, the entire cage can collapse. In contrast, isolated-vm leverages V8’s native Isolate interface. An Isolate is a completely separate instance of the V8 engine with its own memory heap. This provides a much stronger, more primitive form of separation enforced at the C++ level of the JavaScript engine itself, not just at the script level. It’s a much more solid foundation for security because the isolation is built-in from the ground up rather than being layered on top.
Even with more secure libraries, a defense-in-depth approach using tools like Docker is often recommended for true isolation. Could you provide a step-by-step overview for implementing this layered security and explain the specific risks that containerization mitigates which a library-level sandbox simply cannot address?
Defense-in-depth is non-negotiable when dealing with untrusted code. Even the maintainers of vm2 recommend it. The first step is to never run your application directly on a host machine. Instead, you containerize it using a tool like Docker. This wraps your entire Node.js application, including the vm2 library, inside an isolated environment with its own filesystem and network stack. From there, you apply further restrictions: create a dedicated, unprivileged user inside the container so the process isn’t running as root. You should also use security profiles like AppArmor or seccomp to severely limit the system calls the process is allowed to make. Finally, configure strict network policies to prevent the container from making unexpected outbound connections. This layered approach mitigates risks a library sandbox can’t touch. If an attacker achieves a full sandbox escape and gets arbitrary code execution like with CVE-2026-22709, they are still trapped inside a low-privilege, heavily restricted container, unable to access the host system or pivot to other parts of your network.
What is your forecast for the future of JavaScript sandboxing and the ongoing cat-and-mouse game between developers building secure environments and researchers discovering new bypasses?
My forecast is that this cat-and-mouse game will only accelerate. As more applications rely on running third-party or user-submitted code, the demand for sandboxing will grow, but so will the attention from security researchers. I believe we’ll see a gradual shift away from purely proxy-based sandboxes like vm2, which have proven brittle, toward solutions that leverage lower-level engine primitives like V8 Isolates or even technologies like WebAssembly for stronger guarantees. However, no software solution will ever be perfect. The most important trend I hope to see is a broader cultural shift among developers toward assuming that their sandbox will be bypassed eventually. This mindset forces the adoption of a defense-in-depth architecture, where a single library failure is not a catastrophic event but merely one broken link in a much stronger security chain. True security won’t come from a single “unbreakable” sandbox but from layers of pragmatic, hardened isolation.