

The recent discovery of an unaddressed security vulnerability in Anthropic's SQLite Model Context Protocol (MCP) server has reverberated through the tech and cybersecurity communities. Anthropic, a prominent AI company known for breakthrough models like the AI assistant Claude, is under scrutiny
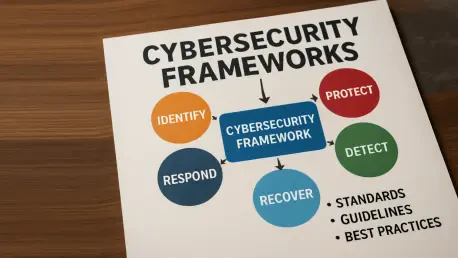
The digital age is marked by an ever-growing reliance on technology and interconnected systems, creating an urgency for robust cybersecurity measures. Within this framework, the Common Vulnerabilities and Exposures (CVE) program plays an indispensable role. However, recent concerns raised by

The intricate relationship between geopolitical tensions and cyber warfare has steadily intensified, placing cyberattacks at the forefront of global security concerns. Nation-state-backed actors have elevated digital offensives, matching the scale and intensity of a physical conflict. As cyber

Against the backdrop of increasing cybersecurity threats, manufacturing sectors, particularly steel production, face profound challenges in safeguarding their operations. The cyberattack on Nucor, a dominant U.S. steel manufacturer, underscores the vulnerabilities inherent in an industry

Despite considerable advancements in security measures, the realm of cloud security continues to be challenged by significant vulnerabilities. In today's digital-centric world, understanding these vulnerabilities is crucial as businesses increasingly depend on cloud technologies. Recent findings

In the realm of IT security, Secure Shell (SSH) keys, often overshadowed by more conspicuous security measures, have emerged as critical components for secure remote access and server management. These keys, pivotal to the automation processes within vast DevOps pipelines, are frequently mishandled

In today's digital landscape, cyber threats are continuously evolving, posing significant challenges for individuals and organizations striving to secure their online presence. Among these threats is the Fake Cloudflare Turnstile exploit, a cunning attack designed to capitalize on misinformation

In today’s digital age, the security of operational technology (OT) environments is more crucial than ever. Rupert Marais, our in-house Security specialist, brings a wealth of expertise in cybersecurity strategies, endpoint and device security, and network management. With increasing attention on

In a rapidly evolving cybersecurity landscape, having robust penetration-testing tools is crucial for organizations to identify vulnerabilities in their systems. The TeamFiltration Framework has emerged as a prominent name in this arena, particularly for its capabilities in breaching Microsoft

Recent fluctuations in the operating system landscape have prompted a growing debate between choosing Microsoft's latest offering, Windows 11, or switching to an increasingly favored alternative, the Linux Plasma Desktop. With Microsoft's strategic push emphasizing Windows 11, marked by substantial
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy