

Modern enterprises frequently grapple with the inertia of legacy systems that fail to meet the rapid demands of a high-velocity digital economy where milliseconds define competitive advantage. Unisys has responded to this challenge by orchestrating a fundamental pivot away from traditional

Rupert Marais brings a wealth of experience to the table when it comes to the shadowy world of cybercrime infrastructure. As an expert in endpoint security and network management, he has watched the ebb and flow of criminal groups as they navigate law enforcement crackdowns and internal power

A routine commute through the heart of London’s King’s Cross station took a turn toward the surreal when an off-duty detective noticed a peculiar green glow emanating from a nondescript suitcase. This single observation in March 2025 proved to be the unraveling of a multi-million pound criminal

The silent digital gears that power modern civilization—electricity, water, and telecommunications—are no longer just mechanical systems but are now the primary targets of a new breed of invisible, state-sponsored warfare. As the boundary between physical safety and digital integrity vanishes, the

The digital infrastructure of the modern world currently finds itself in the crosshairs of a sophisticated and rapidly maturing cyber threat known as CVE-2025-55182, or more colloquially, React2Shell. What began as a theoretical risk in late 2025 has transitioned into a primary instrument for

The rapid proliferation of artificial intelligence has created a landscape where the speed of deployment frequently outpaces the fundamental requirements of digital safety. While most public concern centers on the possibility of a chatbot providing a restricted recipe or a biased answer, the actual

The rapid acceleration of artificial intelligence has created a profound tension between its transformative potential and the fundamental principles of data privacy, a conflict compelling organizations to confront how they manage and protect sensitive information. This dynamic is no longer

Today we're joined by Rupert Marais, our in-house security specialist with deep expertise in cybersecurity strategy and network management. As organizations increasingly find their most valuable data targeted by sophisticated AI-driven scraping, the old playbook of treating it as a low-level

The provocative assertion that a sophisticated F-35 fighter jet could be manipulated with the same fundamental approach as an iPhone signals a profound shift in the landscape of global defense. This statement, from a high-ranking European official, is more than a technical boast; it is a
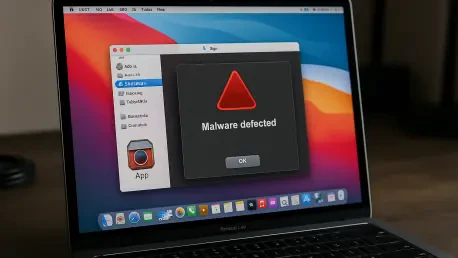
The open-source software ecosystem, built on a foundation of collaborative development and shared trust, has become an unexpected battleground where threat actors are now cleverly disguising malware within seemingly legitimate projects. A recent cybersecurity investigation has uncovered a
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy