

Understanding the ClickFix Campaign in the Hospitality Sector The hospitality industry, a cornerstone of global commerce, faces an escalating threat from sophisticated cybercrime campaigns, with the ClickFix operation emerging as a particularly insidious challenge. This campaign specifically

What happens when machines don’t just follow commands but start making decisions, acting independently across enterprise systems? In 2025, agentic AI—autonomous intelligent systems that reason, decide, and interact—has woven itself into the fabric of business operations, promising unparalleled

In an era where cyber threats evolve at an unprecedented pace, driven by artificial intelligence and sophisticated attack methodologies, organizations face an uphill battle to safeguard their digital assets. Imagine a scenario where a ransomware attack, orchestrated with AI precision, cripples an

In a digital landscape where data breaches and privacy concerns dominate headlines, securing sensitive communications has never been more critical for businesses, and imagine a scenario where a single intercepted email containing proprietary information could jeopardize an entire organization’s

In an era where drones are transforming industries like delivery, agriculture, and disaster response, the looming threat of cyberattacks has cast a shadow over their potential, with hackers capable of hijacking these devices and causing catastrophic failures. Drones, once seen as mere gadgets, now

In a digital landscape where cyber threats evolve at an alarming pace, a recent discovery of critical zero-day exploits targeting Cisco’s Secure Firewall software has sent shockwaves through the cybersecurity community, highlighting the urgent need for immediate action. These vulnerabilities,

In an era where digital content shapes perceptions, a staggering reality emerges: AI-generated videos are now so lifelike that distinguishing fact from fiction has become a daunting task, and Sora 2, a groundbreaking generative AI tool developed by OpenAI, has taken video creation to unprecedented
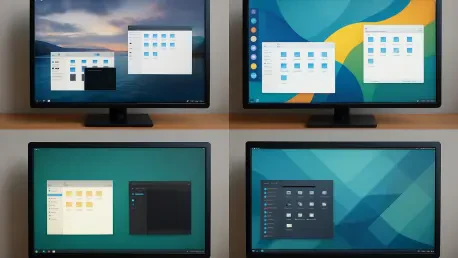
In an era where Linux desktop environments often feel like echoes of decades-old designs, a staggering statistic emerges: over 70% of Linux users express a desire for more modern, customizable interfaces that rival the polish of proprietary systems. Enter the COSMIC Desktop Environment, a bold

I'm thrilled to sit down with Rupert Marais, our in-house security specialist with deep expertise in endpoint and device security, cybersecurity strategies, and network management. With a particular focus on the Android ecosystem and Samsung Knox technologies, Rupert is here to unpack how this

The digital landscape is under siege as malware evolves at an unprecedented pace, with AI technologies fueling a new wave of cyber threats that challenge even the most robust defenses. A startling revelation has emerged about PROMPTFLUX, a malware that leverages Gemini AI to rewrite its code
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy