

Making a routine backup copy of your data is crucial to ensure your information remains available even if something goes wrong. You can automate the backup process, but you also have the option to create backups manually. The primary objective of a backup is to create an image of the selected data

In a recent cyber incident, Mukesh, the CTO of Razz Security, exploited a significant security vulnerability to gain full server access through Continuous Integration/Continuous Deployment (CI/CD) pipelines. CI/CD pipelines streamline the process of delivering code by automating continuous

In the ongoing debate about the effectiveness of built-in antivirus software compared to their paid counterparts, recent findings suggest that built-in solutions offer equally robust protection. Built-in antivirus programs on Microsoft and Apple devices, namely Microsoft Defender Antivirus and

As organizations increasingly recognize the critical role of application security, strategies to ensure the integrity of their software supply chains have become paramount. The 2024 State of Code Security survey, commissioned by OpenText and conducted by Dark Reading, underscores this shift towards
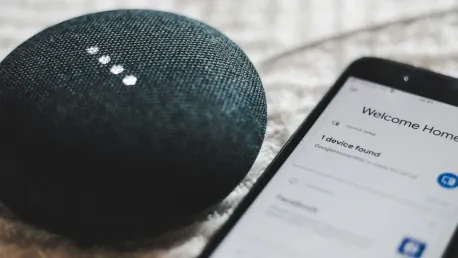
The recent integration of ADT's new ADT+ security system with Google Home promises to restore some of the lost functionalities from the discontinued Nest Secure system. Initially reported in July, this revamped hardware now brings Google Home routines back into the fold, significantly enhancing the

The eagerly anticipated launch of Apple's iPhone 16 has created a buzz among tech enthusiasts worldwide. Unfortunately, this excitement has not gone unnoticed by cybercriminals who have devised various schemes to exploit unsuspecting consumers. This article delves into the various tactics

The landscape for financial technology (FinTech) companies and the European Union's (EU) technological competitiveness is undergoing significant shifts. Both sectors face unprecedented challenges and opportunities. Increasing regulatory scrutiny is placing FinTech firms, especially startups, under

In the digital age, operational technology (OT) environments have become increasingly reliant on remote access solutions to maintain efficiency and streamline operations. The growing adoption of these tools, however, introduces substantial cybersecurity risks, particularly within critical

In recent research conducted by Zerto, it has become increasingly evident that companies are facing significant shortcomings in their disaster recovery and cyber recovery strategies. The findings highlight a troubling trend where backup-related issues have emerged as the primary cause of data loss
Cloud computing has become an indispensable part of daily life, powering everything from video streaming to virtual meetings. Yet, while it offers numerous operational advantages, its energy and environmental impact are significant. This article dives deep into how cloud computing influences both
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy