

The widespread adoption of multifactor authentication has long been championed as a critical bulwark against account takeovers, but a formidable new threat known as "Starkiller" is demonstrating the limitations of this security standard. This advanced Phishing-as-a-Service (PhaaS) tool represents a

The Hype vs. Reality: A Cautious View on the AI Revolution While the public narrative is dominated by the explosive growth of artificial intelligence, a leading voice in cybersecurity is urging a more measured perspective. Nikesh Arora, CEO of Palo Alto Networks, contends that despite the

97% of executives use personal devices to access their work accounts, but these aren’t designed to defend against espionage, zero-click exploits, or data exfiltration. So convenience has come with a tradeoff of vulnerability. In today’s hybrid world, the smartphone in a leader’s pocket holds

The sophisticated tools of digital surveillance, once confined to the shadowy arsenals of government intelligence agencies, are now being packaged, marketed, and sold on the open market to anyone with a few hundred dollars and a malicious intent. This research summary examines the alarming
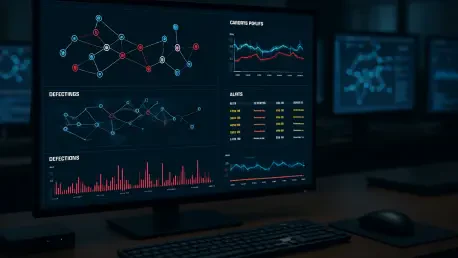
Stepping into the high-stakes world of a modern Security Operations Center (SOC) reveals a complex battleground where analysts race against time to decipher cryptic clues left by sophisticated adversaries. This exploration delves deep into the daily workflow of these digital defenders by

The line separating a nation's most guarded digital secrets from the open market is often just one person's compromise, a single decision that can rebalance global power in the shadows of cyberspace. When a trusted executive within the military-industrial complex chooses personal profit over

The charged atmosphere of the Asia Pacific Network Information Centre's Annual General Meeting was a clear testament to a governance model functioning not just in theory but in vibrant, often contentious, practice. Far from a ceremonial gathering, the event saw members pose sharp, unvarnished

The same artificial intelligence designed to streamline daily life and innovate industries is now being quietly repurposed in the digital shadows to orchestrate sophisticated cyberattacks. Recent findings from Google's own threat intelligence teams have confirmed a troubling trend: state-sponsored
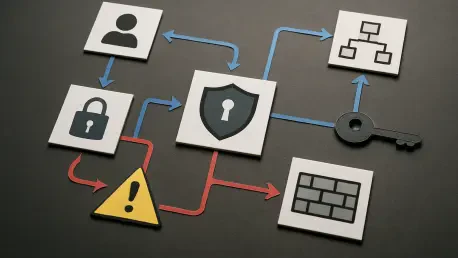
The digital drawbridge and castle walls of traditional cybersecurity are proving increasingly ineffective against an enemy that already possesses the keys to the kingdom. In a landscape where nearly 80% of all breaches leverage compromised credentials, the focus of cybersecurity is shifting from

A single, maliciously crafted request sent across the internet could be all it takes for an attacker to seize complete control of an organization's most sensitive access management systems. This is the stark reality presented by a newly discovered vulnerability in BeyondTrust's core products, a
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy