
The conventional wisdom of building digital fortresses to protect sensitive information is rapidly becoming obsolete in an environment where the primary threat is no longer the breach of a perimeter but the behavior of those inside it. This research summary distills the collective, battle-tested

The digital landscape of 2025 was fundamentally reshaped by a series of seismic security events that exposed deep-seated vulnerabilities across global infrastructure, private enterprises, and even the governmental bodies tasked with protecting them. Throughout the year, organizations grappled with

With a distinguished career centered on endpoint security and network management, Rupert Marais has become a leading voice in deciphering complex cyber threats. His expertise lies in connecting seemingly disparate incidents to reveal underlying trends in the threat landscape. In this conversation,

Today we’re sitting down with Rupert Marais, our in-house security specialist, to dissect a critical vulnerability that’s sending ripples through the AI development community. Known as LangGrinch, this flaw in the popular LangChain framework highlights the dangerous intersection where large

From Responsible Disclosure to a Damaging Accusation The swift integration of artificial intelligence into customer service has opened a Pandora's box of cybersecurity challenges, as one high-speed rail operator recently discovered in a very public and contentious fashion. The rapid adoption of
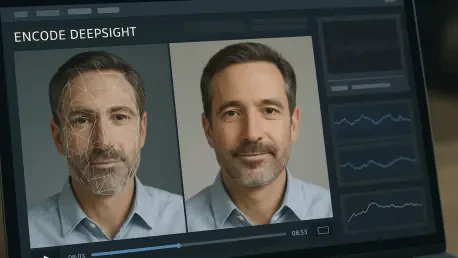
The rapid sophistication of deepfake technology has transformed what was once a social media novelty into a critical security vulnerability for businesses that depend on digital identity verification for their core operations. As synthetic media becomes more accessible and convincing, conventional