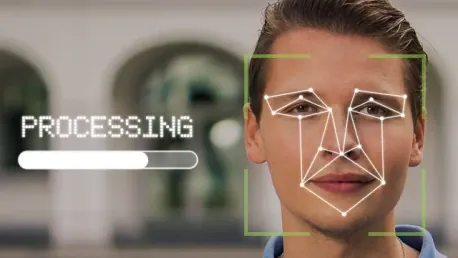
In today's digital age, the rise of deepfake technology poses significant challenges. Deepfakes, which use artificial intelligence to create realistic but fake videos and audio recordings, have become increasingly sophisticated and harder to detect. This article aims to inform readers about how

In an ever-evolving digital landscape fraught with cyber threats, organizations must constantly innovate to stay ahead of potential breaches. Contrast Security's new tool, Application Vulnerability Monitoring (AVM), is poised to significantly enhance how we protect applications in production

Open Source Software (OSS) has become an integral part of modern digital infrastructure, powering nearly 90% of code bases and constituting 70-80% of the material in many applications. However, this widespread adoption has also introduced significant security challenges. As we look ahead to 2025,

In response to an increasing number of sophisticated cyberattacks on U.S. federal agencies, critical infrastructure providers, and high-profile individuals, the Biden administration has released a comprehensive executive order aimed at bolstering cybersecurity across various sectors. Issued on

Cybercriminals spare no industry, targeting sectors like healthcare, insurance, automotive, and education. Healthcare has been a frequent target, with attacks like the Ascension breach last year and the CVR incident in late 2024. Now, the education technology giant PowerSchool has become the latest

A massive data leak affecting Ukrainians and Russians residing in Portugal has recently come to light, raising concerns about targeted vishing scams. The Association of Ukrainians in Portugal has lodged a formal complaint with the National Data Protection Commission (CNPD) after numerous immigrants