
In an era where cyber threats evolve at an unprecedented pace, consider a scenario where a major financial institution suffers a devastating breach, not from an unpatched server, but through a forgotten administrator account with unchecked privileges. This incident, mirroring countless real-world

In the intricate and rapidly shifting world of IT security, a subtle yet profoundly dangerous issue has emerged as a critical concern for organizations worldwide: the persistent access rights known as standing privilege. These always-on permissions, often granted to users or systems without a
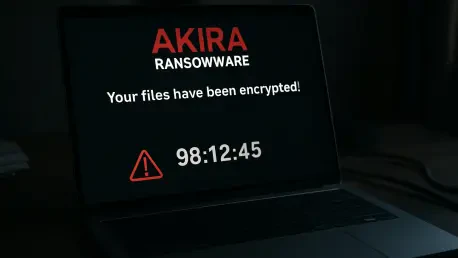
What happens when a trusted shield becomes the very gateway for chaos? In the realm of cybersecurity, SonicWall SSL VPN appliances, long relied upon for secure remote access, have turned into prime targets for a ruthless adversary: the Akira ransomware group. Since late July, these devices have

What if the very tools trusted to streamline daily tasks turned against their users, quietly siphoning off sensitive data like emails and invoices? This chilling reality has struck hundreds of organizations as a once-reliable AI server, designed to manage email workflows, has been exposed as a

In the ever-evolving digital realm, WordPress stands as the backbone of countless websites, commanding an impressive 60.8% market share among content management systems (CMS), and its ubiquity makes it an irresistible target for cybercriminals. Powering everything from personal blogs to sprawling

In an era where artificial intelligence is reshaping enterprise operations, a staggering 80% of companies have encountered unintended actions from AI agents, ranging from unauthorized access to critical data leaks, highlighting the urgent need for robust security measures. These autonomous