
Today, we're joined by Rupert Marais, our in-house security specialist with deep expertise in endpoint security and network management. We're diving into the recent Fortinet zero-day vulnerability, CVE-2026-24858, a critical issue that sent ripples through the security community. Our conversation
A recently disclosed security flaw in the SmarterTools SmarterMail email software has rapidly escalated into a significant threat, with active exploitation observed in the wild merely two days after the vendor released a patch intended to resolve it. This alarming development highlights a

The persistent and evolving nature of cyber threats often means that even the most diligent security patching may not provide the impenetrable defense organizations expect. Fortinet has recently confirmed this unsettling reality by announcing that it is actively working to address a FortiCloud

The very tools designed to protect digital environments have become the conduits for a sophisticated cyberattack, turning a trusted antivirus solution into an unwitting distributor of malware that evades conventional security checks. A recent investigation has uncovered a critical supply chain
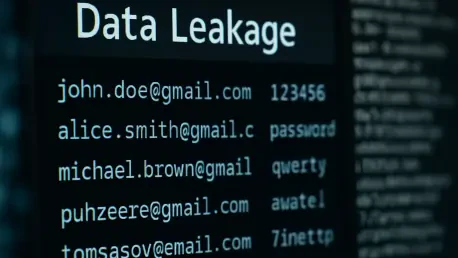
A security incident of staggering proportions came to light in January 2026, revealing that a publicly accessible dataset contained the usernames and passwords for an estimated 48 million Gmail accounts. This massive collection of credentials was part of an even larger dump totaling 149 million

A meticulously orchestrated phishing campaign promising quick financial relief is systematically dismantling the digital security of bank customers across Latin America, turning the hope for a loan into a nightmare of stolen credentials. This operation, first identified in Peru, has rapidly evolved