
Today, we're joined by Rupert Marais, our in-house security specialist, whose expertise in endpoint security and cybersecurity strategy offers a critical perspective on the rapidly changing digital threat landscape. We'll be exploring a series of bold, out-of-the-box predictions for the coming

The digital equivalent of a starting pistol fired across the globe when Microsoft released an urgent security update, giving network defenders a head start that lasted a mere seventy-two hours before sophisticated attackers began their assault. This recent incident highlights a terrifying reality

In the constantly evolving landscape of digital threats, cybercriminals are increasingly turning to unconventional methods to breach corporate defenses, with a recent campaign demonstrating how an innocuous file type can become a powerful weapon for infiltration. Security researchers have

Today, we're joined by Rupert Marais, our in-house security specialist whose extensive experience in endpoint security and network management gives him a unique perspective on the evolving threat landscape. In our conversation, we will explore the forces behind the recent surge in massive DDoS

A seemingly routine phone call has plunged the popular bakery-cafe chain Panera Bread into a significant cybersecurity crisis, culminating in the alleged online leak of sensitive information belonging to over 5.1 million customers. The incident, orchestrated by the notorious extortion group
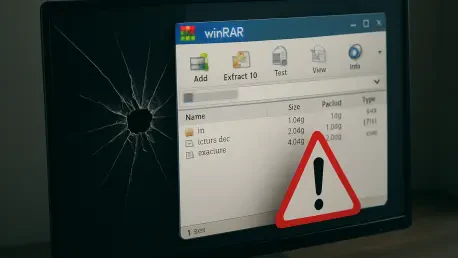
A single, easily exploitable vulnerability within one of the world's most popular file archiving tools has become the common weapon of choice for an astonishingly diverse range of global adversaries. The widespread adoption of this flaw, from elite state-sponsored espionage units to opportunistic