
In the wake of a sophisticated cyberattack campaign that compromised major players like Crunchbase, SoundCloud, and Betterment, we sat down with our in-house security specialist, Rupert Marais. With deep expertise in endpoint security and cyber strategy, Rupert helps us understand the intricate web

Today, we're joined by Rupert Marais, our in-house security specialist with deep expertise in endpoint security and cyber defense strategies. We’ll be diving into the anatomy of the GoBruteforcer botnet, a threat that highlights a startling intersection of modern development practices and
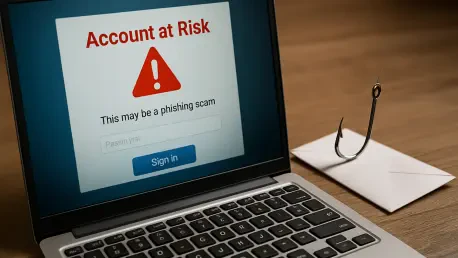
A meticulously crafted deception campaign is now preying on the trust users place in their digital password managers, demanding immediate attention from anyone safeguarding their online life within a LastPass vault. This sophisticated phishing attack underscores a fundamental truth of

We're joined by our in-house security specialist, Rupert Marais, to dissect the latest phishing campaign targeting LastPass users. This attack leverages a potent mix of urgency and social engineering, a timely reminder of the persistent threats facing password manager users. We'll explore the

Firmware, the foundational software that gives life to hardware, has increasingly become a prime target for attackers seeking undetectable persistence on a system. This review will explore the evolution of System Guard Secure Launch, its key features, performance metrics, and its impact on securing

In an unprecedented reversal of roles within the shadowy world of cybercrime, security researchers have successfully turned a potent info-stealing malware’s own infrastructure against its operators by exploiting a critical vulnerability. This strategic infiltration of the StealC malware platform