
Today, we're joined by Rupert Marais, our in-house security specialist whose extensive experience in endpoint security and network management gives him a unique perspective on the evolving threat landscape. In our conversation, we will explore the forces behind the recent surge in massive DDoS

A seemingly routine phone call has plunged the popular bakery-cafe chain Panera Bread into a significant cybersecurity crisis, culminating in the alleged online leak of sensitive information belonging to over 5.1 million customers. The incident, orchestrated by the notorious extortion group
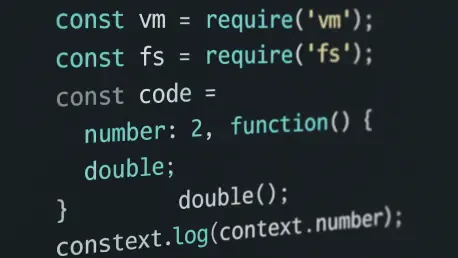
Today, we're joined by Rupert Marais, our in-house security specialist, to dissect a critical vulnerability that has once again shaken the Node.js ecosystem. We’ll be exploring a severe sandbox escape flaw in the popular vm2 library, a tool designed to run untrusted code safely. Our discussion will
A single, easily exploitable vulnerability within one of the world's most popular file archiving tools has become the common weapon of choice for an astonishingly diverse range of global adversaries. The widespread adoption of this flaw, from elite state-sponsored espionage units to opportunistic
The simple act of adding a feature-rich extension to a web browser increasingly invites a hidden digital parasite capable of siphoning finances, stealing data, and compromising the very accounts it promises to enhance. In a landscape where nearly every critical aspect of modern life—from

Across millions of screens worldwide, the endless buffet of on-demand movies and live sports suddenly vanished, replaced not by an error message but by an unnerving silence that signaled the end of an era for some of the world’s largest illegal streaming networks. This was not a system failure but