
With the corporate world more interconnected than ever, the humble email inbox has become the primary battleground for cybersecurity. We sat down with Rupert Marais, our in-house security specialist, to dissect a troubling trend where attackers exploit misconfigurations in Office 365 to impersonate

The brilliant glow of artificial intelligence casts a long and power-hungry shadow over California's energy grid, sparking a high-stakes battle over who will foot the bill for innovation. This article examines the escalating power demands of data centers, focusing on the recent legislative clash

In a move that sent ripples through the international human rights and cybersecurity communities, the United States has quietly removed sanctions from key figures behind one of the world's most notorious commercial surveillance tools. The U.S. Department of the Treasury's decision to lift penalties

In the wake of a staggering data breach at insurance giant Aflac, we sat down with our in-house security specialist, Rupert Marais, to dissect the incident that exposed the personal and medical information of over 22 million people. With deep expertise in endpoint security and cyber strategy,

The intricate network of code running beneath the polished exterior of a modern vehicle holds more personal data than many drivers realize, making a software vulnerability a far more insidious threat than a flat tire. For automotive giant Nissan, this digital reality has become a recurring
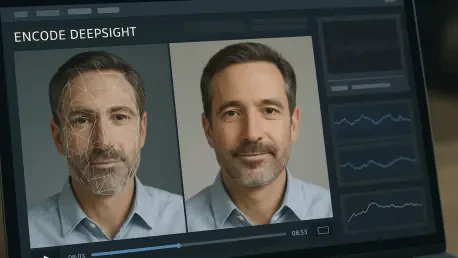
The rapid sophistication of deepfake technology has transformed what was once a social media novelty into a critical security vulnerability for businesses that depend on digital identity verification for their core operations. As synthetic media becomes more accessible and convincing, conventional