
Imagine opening a seemingly harmless app on your Android device, only to unknowingly allow it to snoop on sensitive data from other apps, such as your two-factor authentication codes or personal messages, without any indication of a breach. This chilling scenario is no longer just a hypothetical,

Imagine a digital fortress protecting millions of systems worldwide, yet under constant siege by invisible attackers exploiting every crack in its walls, and in October, Microsoft unleashed its largest Patch Tuesday update ever, tackling a staggering 175 Common Vulnerabilities and Exposures (CVEs).

Imagine a utility company managing power for millions of customers suddenly facing a cyberattack that disrupts service—not through a breach in operational technology, but via a forgotten SharePoint folder containing sensitive engineering diagrams. This scenario is not far-fetched in an era where

Imagine a world where a simple conversation with an AI chatbot could land someone behind bars, a reality unfolding today as evidenced by a startling case at Missouri State University. This isn't a futuristic dystopia but a present concern, where a student, caught in a web of poor decisions, turned

Navigating the Digital Defense Line in the NFL Imagine a scenario where a single misplaced device, like an iPad left unattended at a stadium, exposes sensitive game plans of an NFL team to the public during a critical playoff run, highlighting the very real risks in today’s digitally driven sports
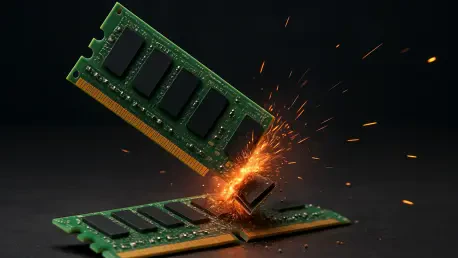
What if the very technology safeguarding the world's most sensitive data in the cloud could be undone by a gadget costing less than a night out? A startling discovery by researchers has unveiled a $50 hardware attack, dubbed "Battering RAM," capable of piercing the defenses of Intel and AMD’s