
A recent and comprehensive security disclosure has cast a harsh spotlight on the inherent risks of self-hosted infrastructure, revealing that the popular open-source platform Coolify contains a staggering 11 critical vulnerabilities that could allow attackers to achieve a full compromise of the
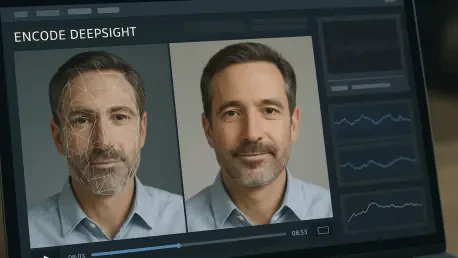
The rapid sophistication of deepfake technology has transformed what was once a social media novelty into a critical security vulnerability for businesses that depend on digital identity verification for their core operations. As synthetic media becomes more accessible and convincing, conventional
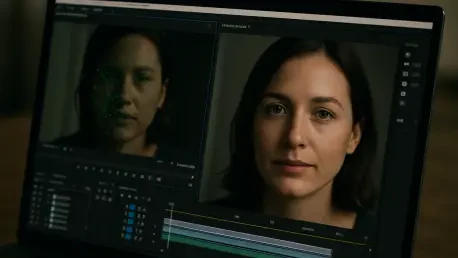
In a bustling digital landscape where viral content can shape opinions in mere hours, a chilling scenario emerges: a video of a political leader making a shocking statement spreads across social media, only to be revealed as a fabrication. Yet, the damage is done—public trust erodes, and chaos

In an era where artificial intelligence is reshaping the digital landscape, a sobering reality has emerged for businesses worldwide: the same technology driving innovation is also fueling unprecedented cyber threats. Lenovo's latest insights, drawn from their third Work Reborn report, paint a stark

In today’s digital age, children are more connected to the internet than ever before, using it for everything from schoolwork to socializing and entertainment, which exposes them to a range of potential dangers that can be difficult for parents to monitor. The online world, while offering

In an era where digital connectivity underpins nearly every aspect of daily life—from financial transactions to critical infrastructure management—the importance of robust cybersecurity cannot be overstated. As reliance on networked systems deepens, so too does exposure to an array of sophisticated