
As the winter chill settled over Poland late last year, a far more menacing threat was silently unfolding in the digital realm, targeting the very infrastructure designed to keep the nation warm and powered. On December 29 and 30, 2025, a sophisticated cyberattack aimed to cripple two major

A single compromised password can unravel an entire digital life in minutes, a reality that has become starkly apparent as cybercrime reports continue to climb, yet remarkably common and weak passwords like '123456' persist in widespread use. In this environment, relying on a password alone is akin

A little-noticed disclosure within a routine corporate transparency report has brought a critical privacy issue to light, revealing that Microsoft turned over customer BitLocker encryption recovery keys to U.S. law enforcement 703 times in the latter half of 2023 alone. This figure, representing
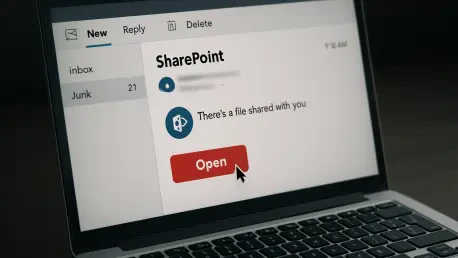
The very digital collaboration tools designed to foster productivity and seamless information sharing are increasingly being weaponized by sophisticated threat actors, turning trusted platforms into Trojan horses for widespread cyberattacks. A recent, highly-coordinated campaign has brought this

As organizations accelerate their digital transformation initiatives, the proliferation of web applications—from vital customer-facing portals to critical internal management systems—has dramatically expanded the digital attack surface, making them a primary target for increasingly sophisticated

Today, we're sitting down with Rupert Marais, our in-house security specialist whose expertise spans everything from endpoint and device security to broad cybersecurity strategy and network management. We'll be delving into the increasingly sophisticated world of phishing and business email