
A critical remote code execution vulnerability within React Native’s development environment is being actively weaponized by threat actors to deploy sophisticated malware, creating a significant and largely unaddressed risk for developers across Windows and Linux platforms. Despite active

Microsoft is fundamentally reshaping its ubiquitous operating system with a series of aggressive security updates that prioritize modern threat protection, a strategic pivot that is causing significant disruption for older systems and established enterprise environments. This bold initiative marks

As immense fortunes become increasingly digitized, the world's wealthiest individuals find themselves in the crosshairs of a new and sophisticated breed of predator operating in the borderless realm of cyberspace. The days of generic, scattergun cyberattacks are long gone; today, high-net-worth

A digital screen on a public bus flashes an arcane error message instead of its usual advertisements, a small disruption that technology experts and urban observers agree offers a surprisingly deep insight into the complex systems governing modern life. This single event, a screen displaying a

With us today is Rupert Marais, our in-house security specialist whose expertise in endpoint security and network management gives him a frontline view of the challenges facing corporate IT. We'll be delving into the increasingly chaotic world of Microsoft's patching cycle, exploring the real-world
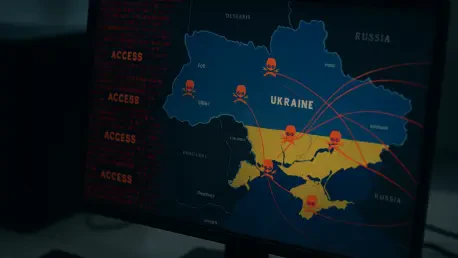
The digital battlefield has once again intensified as a notorious state-sponsored hacking group demonstrated alarming agility by turning a newly disclosed software flaw into a weapon against high-value government targets in less than twenty-four hours. This rapid exploitation marks a significant