
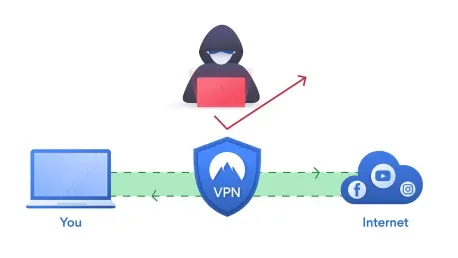
In today's digital age, securing communication channels is paramount. Two popular methods for achieving this are SSH Tunneling and VPNs. Both these technologies offer unique advantages and limitations, making it essential for users to understand their functionalities. This understanding can help
The recent surge in VPN usage has been closely connected to user attempts to bypass new age verification laws affecting access to adult content websites. This trend is particularly prominent in the United States, with Florida standing out as a key example. Google Trends data showcases a notable

The American government’s recent actions against TikTok highlight growing concerns over Chinese applications and their data security practices. As political and social pressure mounts, another Chinese app, Red Note, has begun attracting users in the United States, sparking similar fears. This surge

In a world constantly threatened by cyberattacks, the launch of Tenex.AI Inc.'s managed detection and response (MDR) service marks a pivotal moment in the cybersecurity landscape. Emerging from the shadows with the support of notable backers like Andreessen Horowitz, Shield Capital, and angel

East Hill Elementary School in Montreal’s Rivière-des-Prairies is taking significant steps to ensure elementary students are well-equipped to navigate the digital world safely and responsibly. They are doing this through their innovative Digital Literacy/Online Safety initiative, which is a key

The Consumer Financial Protection Bureau (CFPB) has taken significant enforcement actions against Block, Inc., the company behind Cash App, following extensive investigations into the app's operational conduct. The investigation revealed substantial security and consumer protection failures,