The security of the global cloud infrastructure often rests on the integrity of its most fundamental building blocks, and a critical vulnerability discovered in AWS CodeBuild served as a powerful reminder of how a seemingly minor error can create a significant supply chain risk. This flaw, dubbed “CodeBreach,” exposed a weakness in the continuous integration and continuous delivery (CI/CD) pipelines used by several core AWS open-source projects. By exploiting this vulnerability, an unauthenticated attacker could have potentially injected malicious code into trusted repositories, forging a direct path to compromise the AWS Console itself and the countless customer environments that depend on it. This incident underscores the urgent need for robust security practices within the automated systems that build and deploy modern software.
An Emerging Threat in the Software Supply Chain
The “CodeBreach” vulnerability brought to light the latent dangers lurking within automated CI/CD pipelines, which have become the backbone of modern software development. These pipelines are entrusted with building, testing, and deploying code, often with highly privileged access to source code repositories and production environments. When not properly secured, they transform from an asset of efficiency into a primary target for supply chain attacks.
This analysis will deconstruct the CodeBreach flaw to understand its mechanics, evaluate the potential blast radius of such an attack, and distill the events into actionable security lessons. By examining how a simple misconfiguration could have led to a widespread compromise, organizations can better fortify their own development pipelines against an increasingly sophisticated threat landscape. The lessons learned from this near-miss are not exclusive to AWS users but are universally applicable to any team that relies on automated build systems.
The Potential Impact Gauging the Risk to the AWS Ecosystem
Misconfigurations within CI/CD pipelines represent one of the most pressing threats to software supply chain security. These systems are critical control points that connect source code to live production services, making them high-value targets. A single compromised pipeline can grant an attacker the ability to inject malicious code into a trusted software package, which is then unknowingly distributed to millions of downstream users, creating a cascading security failure.
The potential consequences of the CodeBreach flaw were immense. The primary target was the AWS JavaScript SDK, a foundational library that is not only used by countless customer applications but also powers the AWS Management Console itself. A successful compromise could have allowed an attacker to introduce backdoored code into the SDK, potentially stealing credentials or manipulating resources within any AWS account accessed through the console. Given that the SDK is present in an estimated 66% of all cloud environments, the scale of this threat highlights the profound and far-reaching impact of a single, well-placed vulnerability.
Anatomy of the Vulnerability and Key Security Practices
Best Practice 1 Implement Strict and Anchored Webhook Filters
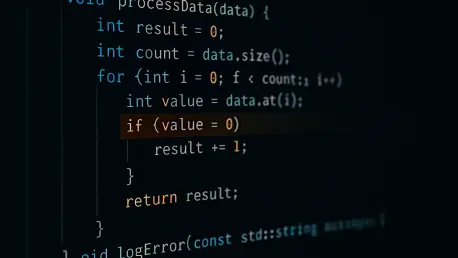
The vulnerability originated from the mechanism AWS CodeBuild used to trigger builds from pull requests on GitHub. To prevent unauthorized code from running in a privileged context, the system relied on an ACTOR_ID filter, designed to ensure that only trusted maintainers could initiate a build. This filter was intended to act as a gatekeeper, verifying the identity of the user submitting the code change before granting access to the build environment.
The core of the flaw, however, was not in the intent but in the implementation. The filter used a regular expression to match the maintainer’s GitHub user ID, but this regex was unanchored. An unanchored pattern checks for a match anywhere within a string, rather than requiring the entire string to match. This subtle but critical error meant that any GitHub user ID that merely contained the trusted ID as a substring would pass the security check. For example, if the trusted ID was “123,” an attacker’s ID like “99123” or “12345” would be incorrectly validated, granting unauthorized access.
Security researchers demonstrated the severity of this issue through a clever exploit. Because GitHub assigns numeric user IDs sequentially, they were able to predict when new user IDs would be created that “eclipsed” the numeric IDs of trusted AWS maintainers. By programmatically creating new GitHub accounts at the right moment, they successfully registered user IDs that contained a valid maintainer ID as a substring. This allowed them to submit a pull request from an untrusted account and successfully trigger a privileged build, completely bypassing the intended security control.
Best Practice 2 Limit Credential Exposure in Build Environments
A fundamental principle of CI/CD security is to minimize the exposure of powerful credentials within build environments. When a build process runs, it often requires access to secrets like API keys or access tokens to interact with other services. If these secrets are loaded into the build’s memory without restriction, they become a prime target for theft if an attacker finds a way to execute arbitrary code, which is precisely what the CodeBreach flaw allowed.
The ability to trigger an unauthorized build was only the first step of the attack chain. Once their malicious pull request was running inside the trusted CodeBuild environment, the researchers were able to execute code that scanned the build’s memory for credentials. They successfully extracted a highly-privileged GitHub token that had been made available to the build process. This token granted them administrative control over the AWS repositories, allowing them to move from simply triggering a build to gaining complete command over the project’s source code.
This escalation of privileges demonstrated a complete takeover of the aws/aws-sdk-js-v3 repository, the foundational library for the AWS Console. Using the stolen credentials, the researchers proved they could have modified code, altered releases, and potentially injected a malicious payload that would have been distributed to a vast number of AWS customers. The incident serves as a stark reminder that even temporary access to a build environment can lead to total compromise if powerful credentials are not properly isolated and restricted.
Conclusion Lessons Learned from a Narrowly Averted Crisis
In response to the responsible disclosure, AWS acted swiftly to remediate the vulnerability. Within 48 hours, the engineering teams had anchored the affected regular expression filters to prevent the bypass, revoked all exposed credentials, and implemented additional memory protections to thwart similar credential theft techniques. This rapid and thorough response was instrumental in ensuring that the flaw was not exploited maliciously and had no direct impact on customer environments.
Ultimately, while direct customer harm was averted, the flaw exposed a critical weakness in the software supply chain that serves as a powerful lesson for the entire industry. The incident revealed how a seemingly insignificant coding error—the omission of just two characters in a regular expression—could create a vulnerability with system-wide implications. It demonstrated that the security of a vast cloud ecosystem can depend on the meticulous implementation of controls in its automated build pipelines.
This event provided clear, actionable recommendations for all organizations utilizing CodeBuild or other CI/CD systems. It underscored the absolute necessity of blocking untrusted pull requests from ever triggering privileged builds, a practice that should be a default security posture. Furthermore, it highlighted the importance of using fine-grained, minimally-permissioned access tokens that grant only the specific access required for a task, thereby limiting the potential damage of a credential leak. Finally, the incident was a definitive case study on the importance of always anchoring regular expression patterns used in security filters to ensure they match exactly as intended.