
The modern healthcare landscape relies heavily on a complex web of interconnected service providers, yet this interdependence often introduces silent vulnerabilities that can jeopardize the privacy of thousands of patients in a single incident. Recently, Vikor Scientific, a South Carolina-based

The digital infrastructure of the modern world currently finds itself in the crosshairs of a sophisticated and rapidly maturing cyber threat known as CVE-2025-55182, or more colloquially, React2Shell. What began as a theoretical risk in late 2025 has transitioned into a primary instrument for
The rapid deployment of autonomous digital entities has fundamentally altered the perimeter of the modern enterprise, turning what were once simple productivity tools into proactive participants with the power to navigate internal networks independently. This transition from traditional logic-based

The financial viability of a modern enterprise now rests on the strength of a single employee’s login credentials rather than the thickness of its digital perimeter walls. While traditional firewalls and endpoint detection remain staples of the security stack, this year marks a definitive shift
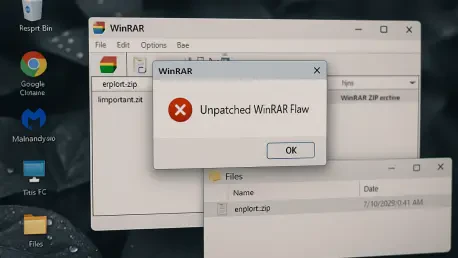
With us today is Rupert Marais, our in-house security specialist, whose expertise in endpoint security and cybersecurity strategies offers a critical perspective on today’s threats. We’re delving into a widespread vulnerability in a piece of software that many of us have used for decades: WinRAR.

What began as a routine day for the finance department quickly unraveled when a seemingly harmless PDF attachment, disguised as a "request order" from a trusted colleague, became the entry point for a major corporate security breach. This incident highlights a dangerous evolution in cybercrime,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55