

The seamless integration of advanced software and connectivity in modern vehicles has transformed them into sophisticated computers on wheels, yet this evolution carries a significant and often overlooked risk. Recent revelations from the annual Pwn2Own competition in Tokyo have cast a harsh light
The very tools meticulously crafted to accelerate innovation and streamline software development are now being systematically turned into covert channels for espionage and sabotage, fundamentally challenging the trust developers place in their daily workflows. A series of sophisticated attacks

The complete digital replica of a human being—encompassing their face, voice, and unique biometric identifiers—is now a commodity traded on the dark web for less than the price of a cup of coffee. This startling reality signals a profound transformation in the digital threat landscape, where

A newly discovered set of three critical zero-day vulnerabilities within the mcp-server-git , a reference implementation for the Model Context Protocol (MCP), has exposed a significant security gap in AI-driven development environments. These flaws, rooted in inadequate input validation and

Today, we're joined by Rupert Marais, our in-house security specialist with deep expertise in endpoint security and cyber defense strategies. We’ll be diving into the anatomy of the GoBruteforcer botnet, a threat that highlights a startling intersection of modern development practices and
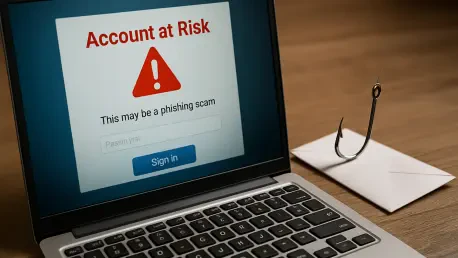
A meticulously crafted deception campaign is now preying on the trust users place in their digital password managers, demanding immediate attention from anyone safeguarding their online life within a LastPass vault. This sophisticated phishing attack underscores a fundamental truth of
The relentless drumbeat of cybersecurity alerts has created a profound paradox where security teams, armed with more data than ever before, find themselves struggling to prevent actual breaches. This predicament stems not from a lack of information but from a crisis of context. For years, the

The rapid integration of artificial intelligence into core business functions has inadvertently created a pervasive and dynamic attack surface that fundamentally bypasses the safeguards of conventional cybersecurity frameworks. As organizations embrace AI to fuel innovation and gain a competitive

The seemingly innocuous calendar invitation popping up on your screen could now be a Trojan horse concealing a dormant payload designed to trick your trusted AI assistant into systematically exfiltrating your most private data. In a startling revelation, security researchers have uncovered a

The intricate and often invisible machinery that purifies drinking water, processes food, and automates manufacturing lines operates on a foundation of trust in digital controllers—a trust that has recently been proven to be dangerously misplaced. A new analysis of a widely deployed industrial
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy