
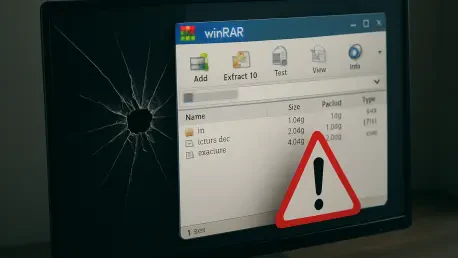
A single, easily exploitable vulnerability within one of the world's most popular file archiving tools has become the common weapon of choice for an astonishingly diverse range of global adversaries. The widespread adoption of this flaw, from elite state-sponsored espionage units to opportunistic

In a world where digital threats evolve by the minute, staying ahead requires more than just software updates; it demands deep, forward-looking expertise. We're joined today by Rupert Marais, our in-house security specialist whose work at the intersection of endpoint security and network defense
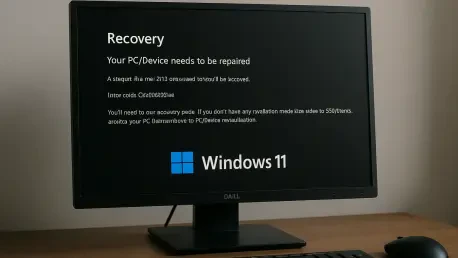
Introduction The sudden and stark appearance of a Blue Screen of Death is an unwelcome sight for any computer user, especially when it prevents the system from starting up at all. Recently, a number of Windows 11 users have encountered this exact scenario, where their machines refuse to boot

The Unseen Threat: Why AI Governance is the New Security Frontier In today's rapidly evolving technological landscape, the enthusiastic adoption of artificial intelligence tools by employees is far outpacing the creation of corporate governance. This gap has given rise to "shadow AI"—the

Today we're joined by Rupert Marais, our in-house security specialist, to unpack the complex and urgent cybersecurity crisis facing Latin America. As the region accelerates its digital transformation, a perfect storm is brewing: a staggering lack of confidence in national cyber defenses, a critical

A fortress is rarely conquered by a frontal assault against its strongest walls; rather, its downfall is almost always assured by a single, unguarded postern gate left carelessly ajar. This timeless principle of warfare holds a profound and urgent truth for modern cybersecurity, where the most

The digital keys to a modern enterprise are not stored in a vault but are scattered across thousands of employee accounts, each secured by a password that may offer little more than the illusion of protection. While security leaders invest heavily in defending against sophisticated cyber threats, a

The persistent and evolving nature of cyber threats often means that even the most diligent security patching may not provide the impenetrable defense organizations expect. Fortinet has recently confirmed this unsettling reality by announcing that it is actively working to address a FortiCloud

The digital fortress of one of the world's most iconic brands has been breached, spilling a treasure trove of sensitive corporate secrets onto the dark web and raising critical questions about the security of its global operations. A ransomware group calling itself "World Leaks" has claimed

A recently disclosed vulnerability within Instagram’s core infrastructure has raised significant questions about the platform's privacy safeguards, revealing that private photos and their captions could be accessed by unauthenticated attackers without needing a login or an approved follower
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy