

The trust placed in a simple software update notification can become a gateway for sophisticated espionage, a reality recently underscored by a targeted attack that turned a trusted developer tool into a weapon. Secure software update mechanisms represent a critical line of defense in the

The rapid adoption of Artificial Intelligence presents a dual-edged sword for the modern enterprise, promising unprecedented efficiency while being fueled by data that organizations often do not fully understand. This article analyzes the critical trend of AI Data Governance, exploring the

A chilling new report reveals a significant escalation in the tactics of state-sponsored cybercrime, as a North Korean threat actor has begun integrating artificial intelligence into highly sophisticated social engineering schemes targeting the cryptocurrency sector. This group, identified as

The unassuming artificial intelligence assistant, now a permanent fixture in countless web browsers, has become an indispensable tool for boosting productivity by summarizing complex articles and drafting professional emails. The trust placed in these everyday productivity tools has been profound,
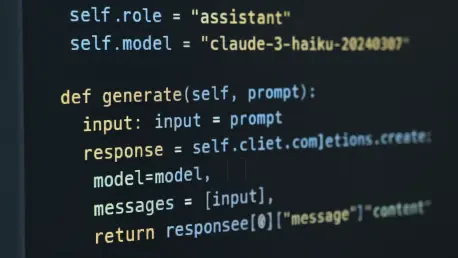
Evaluating the Impact of Claude Code's Controversial UI Update In the rapidly evolving landscape of AI-powered development tools, a single user interface tweak can ignite a firestorm of debate, fundamentally altering the relationship between a developer and their digital assistant. This review

A newly released analysis from Google's Threat Intelligence Group has meticulously detailed a sustained and highly coordinated multi-vector cyber offensive waged against the global defense industrial base, revealing a complex web of state-sponsored espionage and disruption. The comprehensive report

A developer's most trusted toolset can become an adversary's most effective weapon, turning a secure environment for remote collaboration into a hidden backdoor for state-sponsored espionage. This new reality is underscored by a sophisticated campaign where North Korean threat actors have co-opted

A modern vehicle contains more lines of code than a commercial airliner, and a single vulnerability could theoretically mean the difference between a smooth ride and a catastrophic failure. This reality has forced a fundamental reckoning within the automotive industry, where the consequences of a

Recent cyberattacks targeting the widely used SolarWinds Web Help Desk platform have cast a harsh spotlight on a critical vulnerability that many organizations overlook: the inherent risk posed by applications directly exposed to the public internet. A strong consensus among security experts from

The catastrophic cascade of a network-wide security breach can often be traced back to a single, forgotten server left vulnerable by an oversight in routine maintenance. Ransomware exploit chaining represents a significant advancement in offensive cybersecurity tactics. This review will explore the
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy