
Recent reports have unveiled a significant security concern for WhatsApp users, stemming from the emergence of Israeli spyware named Graphite, developed by Paragon Solutions. This spyware has been used to hack into the accounts of journalists and individuals, raising alarms about privacy and data

Concerns over the security and privacy of advanced AI models have reached new heights with recent revelations surrounding DeepSeek-R1, an artificial intelligence model developed by China-based DeepSeek. A comprehensive study identified severe security and safety issues with this AI, which
In today's digital landscape, strong passwords are crucial for protecting your online accounts and sensitive information. As cyber threats evolve, robust password security and the use of password managers are more important than ever, especially for software users and professionals in the United

Recent breaches in healthcare networks, such as those affecting Connecticut's Community Health Center Inc. and California's NorthBay Healthcare Corporation, have exposed over 1.5 million individuals' sensitive data, highlighting the urgent need for enhanced cybersecurity measures in healthcare

The landscape of compliance is undergoing a significant transformation, with modern organizations facing much more stringent enforcement under current U.S. policies and regulations. The shift changes compliance from theoretical guidelines to real threats that have severe consequences for

The unexpected dissolution of the Cyber Safety Review Board (CSRB) under the Trump administration has left the cybersecurity community stunned and concerned. Established by an executive order from the Biden Administration, the CSRB consisted of public and private sector experts who analyzed major

As organizations worldwide grapple with complex and evolving cybersecurity threats, the need for comprehensive and advanced security solutions has become paramount. The landscape of cybersecurity is continuously changing, with sophisticated attackers leveraging new tactics to breach defenses. In

The 30th edition of Infosecurity Europe is set to take place on June 3-5, 2025, at ExCeL London. This milestone event celebrates three decades of cybersecurity advancements and sets the stage for the future of the industry. In preparation for the event, the 2025 Cybersecurity Trends Report reveals

A significant data breach has impacted the Toronto District School Board (TDSB) and multiple school boards across North America. It is particularly concerning due to the vast amount of personal information compromised on the PowerSchool platform. This breach has placed a spotlight on the
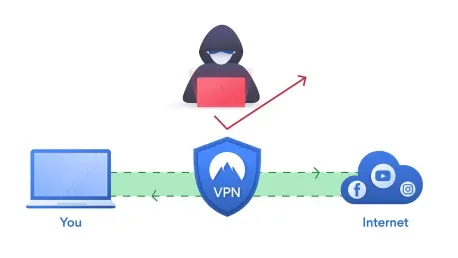
The recent surge in VPN usage has been closely connected to user attempts to bypass new age verification laws affecting access to adult content websites. This trend is particularly prominent in the United States, with Florida standing out as a key example. Google Trends data showcases a notable
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy