

In today's hyper-connected enterprise environment, a staggering reality looms over security teams: the average organization juggles around 1,100 applications, a number that often climbs higher with undetected tools lurking in the shadows, creating a critical challenge for identity governance. This

Hospitals stand as critical pillars of community health, offering solace and healing in times of need, yet they grapple with profound security challenges that jeopardize the well-being of patients, staff, and visitors alike, with threats ranging from violent confrontations to unauthorized

What happens when a single email can unravel a corporation's secrets or a smart thermostat becomes the gateway to stolen blueprints? In 2025, the digital world is a minefield, with cyber threats striking at unprecedented speed and sophistication, making it crucial to understand the evolving

In an era where cyber threats evolve at an unprecedented pace, driven by artificial intelligence and automation, businesses face a daunting challenge to protect data and systems beyond traditional network boundaries, especially as the rise of remote work and mobile devices has shattered the concept

Setting the Stage for a Massive Transition The landscape of enterprise IT is undergoing a seismic shift as over 440,000 SAP customers face an urgent deadline to adapt to changing systems. With support for SAP Identity Manager (SAP IdM) and SAP Governance, Risk and Compliance (SAP GRC) ending by

Today, we’re thrilled to sit down with Rupert Marais, our in-house security specialist with deep expertise in endpoint and device security, cybersecurity strategies, and network management. With the recent introduction of the UK’s Cyber Security and Resilience (CSR) Bill to Parliament, we’re diving

Introduction In an era where smartphones hold vast amounts of personal and professional data, the emergence of cyber threats capable of remotely erasing entire devices is a chilling reality that demands immediate attention from users and security experts alike. A sophisticated campaign by the KONNI
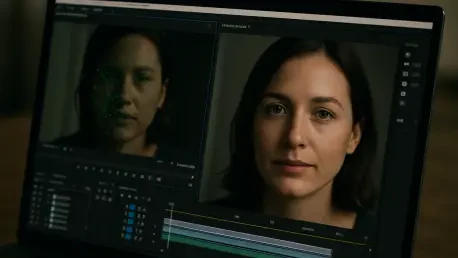
In a bustling digital landscape where viral content can shape opinions in mere hours, a chilling scenario emerges: a video of a political leader making a shocking statement spreads across social media, only to be revealed as a fabrication. Yet, the damage is done—public trust erodes, and chaos

In an era where technology evolves at a breakneck pace, a staggering statistic emerges: over 60% of cybersecurity professionals now report encountering malware created with artificial intelligence tools, pointing to a new frontier in cybercrime. This alarming trend highlights how AI-generated

In an era where technology underpins nearly every aspect of daily life, the reliability of software and cloud services has never been more critical, yet one of the industry’s giants seems to be faltering under the weight of its own ambitions. Microsoft, a company once synonymous with robust
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy