

In the vast and unforgiving landscape of cyberspace, the line between a legitimate command and a catastrophic system compromise can be as thin as a single misplaced letter. A recent, widespread malware campaign targeting users of unofficial software activation tools has starkly illustrated this

The devastating fallout from a major corporate data breach often unfolds over days or weeks, but the 2022 intrusion at LastPass has proven to be a stark and costly exception, with its consequences echoing for years. A comprehensive investigation has now revealed that this single security failure

The intricate network of code running beneath the polished exterior of a modern vehicle holds more personal data than many drivers realize, making a software vulnerability a far more insidious threat than a flat tire. For automotive giant Nissan, this digital reality has become a recurring

The traditional security perimeter is gone. It was not breached by a single attack but dissolved by a thousand strategic business decisions: the shift to the cloud, the rise of the remote workforce, and the integration of third-party SaaS applications into critical workflows. For years, security

In the wake of a significant cyber-attack on a critical NHS supplier, the security of our digital supply chain has never been more scrutinized. We sat down with Rupert Marais, our in-house security specialist, to dissect the complex interplay between data collection, third-party risk, and

With financial scams constantly evolving, we turn to our security specialist, Rupert Marais, for his expertise in cybersecurity and fraud prevention. As criminals increasingly pivot from traditional banking fraud to the less-regulated world of gift cards, consumers are facing new and insidious
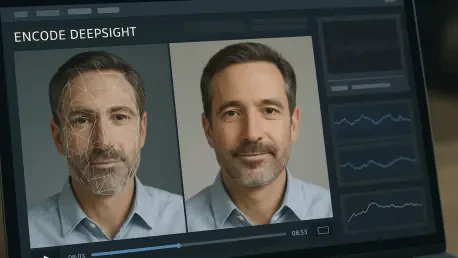
The rapid sophistication of deepfake technology has transformed what was once a social media novelty into a critical security vulnerability for businesses that depend on digital identity verification for their core operations. As synthetic media becomes more accessible and convincing, conventional

A sophisticated phishing campaign leveraging a legitimate but often overlooked Microsoft 365 feature has enabled Russian-aligned hackers to bypass conventional security measures and achieve full account takeovers against critical Western targets. This method, known as device code phishing, subverts

With us today is Rupert Marais, our in-house Security Specialist, whose expertise in endpoint security and cybersecurity strategy offers a vital perspective on digital threats. We’ll be exploring the recent University of Sydney data breach to understand the deeper issues at play. Our conversation

The Dawn of a New IT Paradigm A profound shift is underway in the information technology sector, one that promises to redefine the very nature of IT services. The recent appointment of former Palantir CIO Jim Siders to lead Shield Technology Partners, a new venture backed by over $100 million, is
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy