

The widespread adoption of container-first infrastructure has inadvertently created a profound and dangerous chasm between the speed of digital innovation and the maturity of corresponding security frameworks. While enterprises have universally embraced containers and microservices as the

A single, perfectly timed video call from a chief executive officer, visually and audibly indistinguishable from the real person, has just authorized a multimillion-dollar transfer that will cripple a company before the actual executive even finishes their morning coffee. This is not a speculative
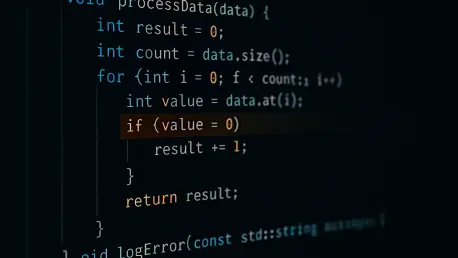
The security of the global cloud infrastructure often rests on the integrity of its most fundamental building blocks, and a critical vulnerability discovered in AWS CodeBuild served as a powerful reminder of how a seemingly minor error can create a significant supply chain risk. This flaw, dubbed
The promise of automated financial management relies on a foundation of digital trust, a foundation recently shaken for over a million investors following a significant security incident. A Crack in the Digital Vault: Understanding the Betterment Security Incident Betterment has built its

We're sitting down with Rupert Marais, our in-house security specialist, to dissect a critical vulnerability that recently sent shockwaves through the enterprise world. This wasn't just another bug; it was a perfect storm where a basic authentication flaw collided with the power of agentic AI,

A shadow economy operating on the blockchain has quietly swelled into a $154 billion industry, driven not just by scattered hackers but by the coordinated efforts of nation-states and sophisticated criminal syndicates. This research summary delves into the explosive 160% growth of the illicit

The silent, interconnected web of automated workflows that powers modern business has quietly become one of the most lucrative and vulnerable targets for cyber adversaries. The rising adoption of workflow automation platforms like n8n is revolutionizing business efficiency, allowing organizations

A massive data theft operation has recently come to light, revealing how two malicious Google Chrome extensions successfully compromised the private information of over 900,000 users by masquerading as sophisticated AI-powered productivity tools. This incident underscores a perilous new reality

Sudden Chaos: How a Digital Expiry Date Paralyzed Logitech Peripherals Countless macOS users recently found their highly customized Logitech peripherals rendered frustratingly basic, as a silent digital deadline passed and threw their workflows into disarray. What began as a normal day quickly

Today we're joined by Rupert Marais, our in-house security specialist, to dissect a long-running espionage campaign targeting some of the world's most critical infrastructure. For years, a sophisticated group known as UAT-7290 has been methodically infiltrating telecommunications networks across
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy